This guide will list the steps to extract the payload.bin file from a stock firmware and make you aware of the benefits of carrying out this extraction. The stock firmware comes in quite a few variants, depending on the OEM to which your device belongs. For instance, while Pixel packs its offerings in a simple ZIP format, Xiaomi has it inside TGZ > TAR > ZIP [yes, it’s a really long journey]. On the other hand, if we talk about OnePlus, then its firmware is released in ZIP followed by payload.bin.
While one could easily extract the likes of ZIP and TGZ via Windows native File Explorer or third-party apps like 7ZIP, the real issue arises with payload as there’s not much support for this file from the third-party apps, let alone the default one provided by the OS. But fret not! In this guide, we will show a couple of nifty workarounds that should help you easily extract payload.bin from the stock firmware in just a few clicks. Follow along for the steps.
Why Should You Extract Payload.bin File?
Upon extracting this bin file, you’ll get all the partition files in their respective BIN/IMG format. But why is there a need to carry out this extraction and where these files will come in handy? Let’s find out!
- Boot/Init_boot: The boot.img [Android 12 or below versions] or the init_boot [Android 13+] could be patched via Magisk and flashed via Fastboot to gain administrative access, in other words, root.
- Vbmeta: The vbmeta.img is required to disable verification and verity checks on your device. This in turn could come in handy while flashing GSI ROMs.
- Modem: You could flash the modem.img or non-hlos.bin file to fix network-related issues on your device.
- Unbrick/Bootloop: If your device is in a bootloop or softbrick state, then these files could be flashed to their respective partitions via Fastboot Commands in both the Fastboot and FastbootD Mode.
- Upgrade/Downgrade: You could also flash these files to carry out update/downgrade, though the latter might not be supported across all devices, so make sure to verify the compatibility beforehand.
How to Extract payload.bin file from Stock Firmware
There exist four methods through which you could get this job done, three of them require Python and the execution of a few commands whereas the last one provides a GUI-based interface and has completely streamlined the extraction process. It’s along the obvious line that the tool-based method is the easiest, shortest, and most straightforward among all the four. Still, we have listed all four methods below, try out the one that is in sync with your requirements.
Via Fastboot Enhance Tool
As already discussed above, this is the shortest and easiest way of getting the job done. So if you are not looking to dive deep into the technicalities of the Python commands, then this would be your go-to method. Apart from that, one major advantage of this approach over all the others is that you get complete control over the bin file as you don’t have to extract the entire payload.bin.
Instead, you could simply select the files that you wish to extract from payload.bin and do the extraction just for those files. For instance, if you want to root your device, then you could only extract the boot or init_boot, as opposed to other methods that will leave you with no choice but to extract the entire bin folder, which would call for unnecessary time and effort. SO owing to all these reasons, this GUI approach is the preferred one for tech enthusiasts.
- To begin with, download the Fastboot Enhance Tool from GitHub [direct link]. and extract it onto your PC.
- Then download the firmware version that is currently installed on your device. You could verify the same via Build Number.
- Once you have got the firmware, get the payload.bin file from there and transfer it inside the Fastboot Enhance Tool folder.
- Now double-click the Fastboot Enhance Tool EXE file to launch it. Then go to Payload Dumper and click Browse.
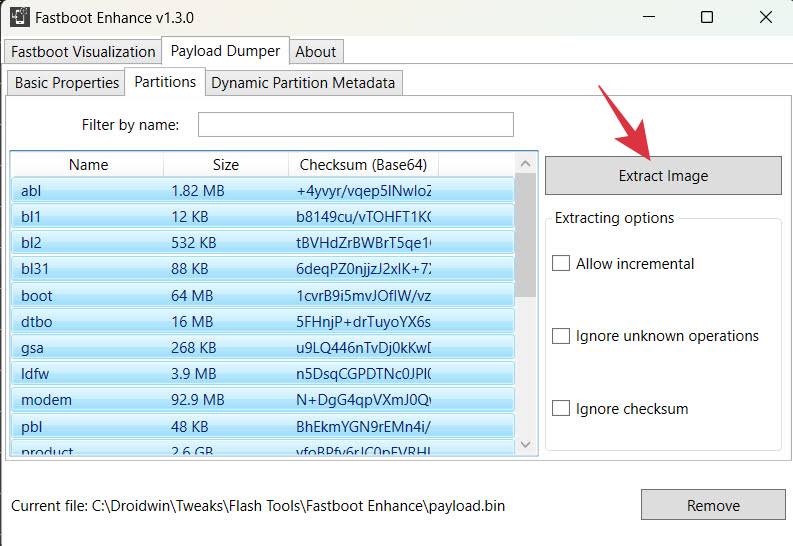
- Select the payload.bin file and hit Open. Now go to the Partitions tab and select the desired file/files that you want to extract.
- Finally, checkmark Allow Incremental and hit Extract Image. Then choose the location where the file should be extracted.
- The process will now start and can take a while depending on the number of files being extracted. Once done, you’ll be notified of the same.
That’s it. These were the steps to extract the payload.bin from stock firmware via the Fastboot Enhance Tool. Let’s now make you aware of the other three methods of carrying out this task.
Via Payload Dumper
- Download Python from its official site and install it onto your PC.
- Make sure to checkmark Add Python to Path on the setup screen.
- Once the installation is complete, check Disable Path Length Limit.
- Now download the Payload Dumper Tool and extract it inside Python.
- If you have chosen the default installation directory, then the path is:
C:\Users\USER-NAME\AppData\Local\Programs\Python\Python <version number>
- Likewise, transfer the stock firmware’s payload.bin inside this folder.
- Now type in the below command to install the requirements.
python -m pip install -r requirements.txt
- Then type in the below command to extract the payload.bin file.
- Once done, you’ll get the extracted files inside the Output folder, which is present in the Python directory.
Default: C:\Users\USER-NAME\AppData\Local\Programs\Python\Python<version-number>/Output
Via Payload Dumper Go
This is the streamlined and easier version of the above tweak and has negated the need to use Python. Here’s how to use this method:
- To begin with, download the payload-dumper-go 1.0.0 from GitHub [Credits: XDA Member ssssut].
- Then extract it to any convenient location on your PC. The name of the file will be along the lines of payload-dumper-go_1.0.0_windows_amd64. Rename it to payload-dumper-go.
- Now, download the liblzma-5.dll file and transfer it to the same folder where the payload-dumper-go.exe file is present.
- After that, transfer the payload.bin file from the stock firmware to this folder.
- So you should have the payload-dumper-go.exe, payload.bin, and liblzma-5.dll files all under this folder.
- Now head over to the folder’s address bar, type in CMD, and hit Enter. This will launch the Command Prompt.
- Then type in the below command to extract the payload.bin file:
payload-dumper-go payload.bin
- The extraction process will now begin and will only take a few seconds.
- Once done, all the extracted files will be placed inside the folder named extracted_date_time that is created inside that directory.
Extract Payload.Bin Without Android
One obvious benefit of this tool is the fact that you don’t need to take the help of a PC to carry out the extraction process. On the flip side though, the process could prove to be a tad bit complicated for some.
- First off, download the Payload Dumper Tool on your device.
- Then extract it in Internal Storage but not inside any folder.
- Now transfer the payload.bin file inside the Payload Dumper folder.
- Then download and install the Termux App on your device.
- Now launch it app and execute the below four commands.
- You might be asked to install additional dependencies, so type in Y, and hit Enter.
pkg install python -y pip install --upgrade pip pip install protobuf apt update && apt upgrade -y
- You might now get a warning from Termux that the “storage partition is going to be wiped but no storage contents will be touched”. Just type in Y and hit Enter. No data will be lost on your device.
termux-setup-storage
- Now change the Termux directory to the folder where the payload.bin file is present. Use the below command for that:
cd storage/shared/payload_dumper
- Install a couple of Google API dependencies via the below command:
pip install google pip install google-api-core
- Finally, use the below command to extract the payload.bin file on your device:
python payload_dumper.py payload.bin
- The extraction will now start. Once done, you’ll get all the files in the payload_dumper folder.
That’s it. These were the four different methods to extract the payload.bin file. All your queries regarding the same are welcomed in the comments section below.